Infographic text included for screen readers:
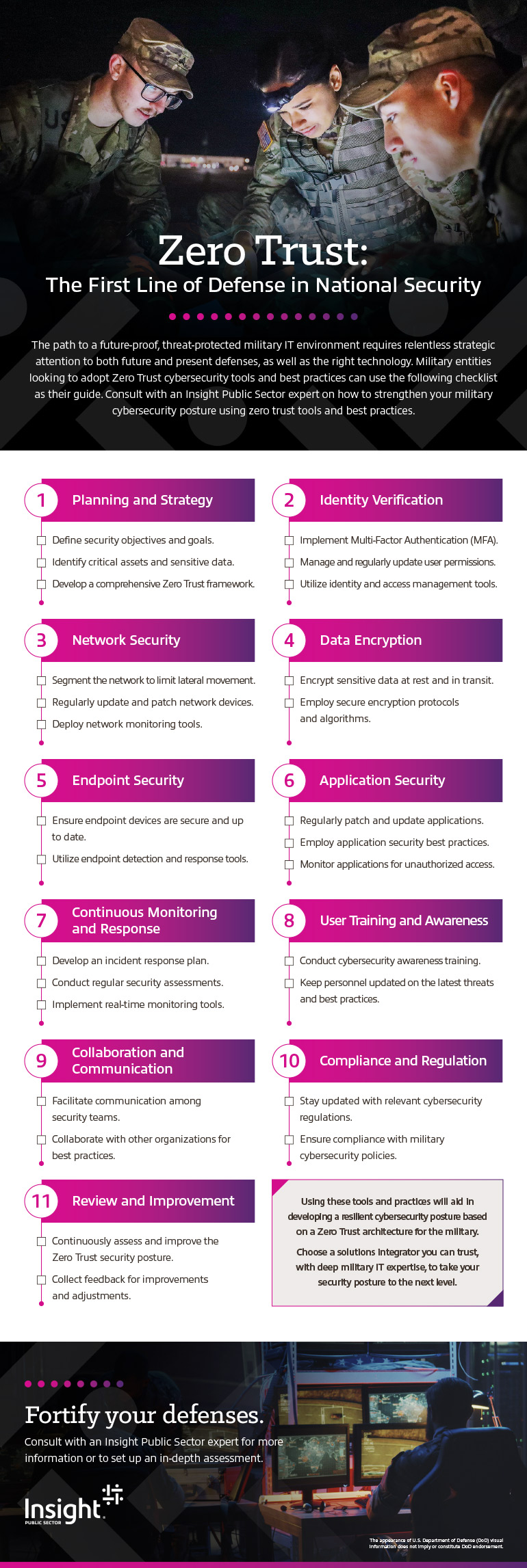
The path to a future-proof, threat protected military IT environment requires relentless strategic attention to both future and present defenses, as well as the right technology. Military entities looking to adopt Zero Trust cybersecurity tools and best practices can use the following checklist as their guide. Consult with an Insight Public Sector expert for an in-depth assessment.
1. Planning and Strategy:
- Define security objectives and goals.
- Identify critical assets and sensitive data.
- Develop a comprehensive Zero Trust framework.
2. Identity Verification:
- Implement Multi-Factor Authentication (MFA).
- Manage and regularly update user permissions.
- Utilize identity and access management tools.
3. Network Security:
- Segment the network to limit lateral movement.
- Regularly update and patch network devices.
- Deploy network monitoring tools.
4. Data Encryption:
- Encrypt sensitive data at rest and in transit.
- Employ secure encryption protocols and algorithms.
5. Endpoint Security:
- Ensure endpoint devices are secure and up to date.
- Utilize endpoint detection and response tools.
6. Application Security:
- Regularly patch and update applications.
- Employ application security best practices.
- Monitor applications for unauthorized access.
7. Continuous Monitoring and Response:
- Develop an incident response plan.
- Conduct regular security assessments.
- Implement real-time monitoring tools.
8. User Training and Awareness:
- Conduct cybersecurity awareness training.
- Keep personnel updated on the latest threats and best practices.
9. Collaboration and Communication:
- Facilitate communication among security teams.
- Collaborate with other organizations for best practices.
10. Compliance and Regulation:
- Stay updated with relevant cybersecurity regulations.
- Ensure compliance with military cybersecurity policies.
11. Review and Improvement:
- Continuously assess and improve the Zero Trust security posture.
- Collect feedback for improvements and adjustments.
Using these tools and practices will aid in developing a resilient cybersecurity posture based on a Zero Trust architecture for the military.
Choose a solutions integrator you can trust, with deep military IT expertise, to take your security posture to the next level.