
View and protect assets in real time
Tenable® is the leading exposure management company. Together, Insight and Tenable can help you gain comprehensive visibility into your attack surface, so you can stay one step ahead of attackers.
Powerful protection. Streamlined features.
Anticipate attacks and reduce cyber risk with Tenable One Exposure Management Platform.

Prioritize.
Advanced analysis and risk-based exposure scoring weighs asset value, criticality, vulnerabilities, and threat context.

Assess.
Quantify your exposure, compare your effectiveness, identify areas of focus, and optimize security investment.

Measure.
Quantify and benchmark your exposure, compare your effectiveness against peers, identify areas of focus and optimize security investment.


Introducing Tenable One: Exposure Management for the Modern Attack Surface
Get holistic protection for your infrastructure, identities, and workloads with Tenable Cloud Security. Tenable Cloud Security is an all-in-one solution that protects your cloud assets across multicloud environments by automating security operations, remediating security gaps, and more.


Unified Cloud Native Application Protection Platform (CNAPP)
Get holistic protection for your infrastructure, identities and workloads with Tenable Cloud Security. Tenable Cloud Security is a single, all-in-one solution that protects your cloud assets across multi-cloud environments by automating security operations, remediating security gaps, and reducing the attack surface through meaningful visualization and step-by-step guidance.
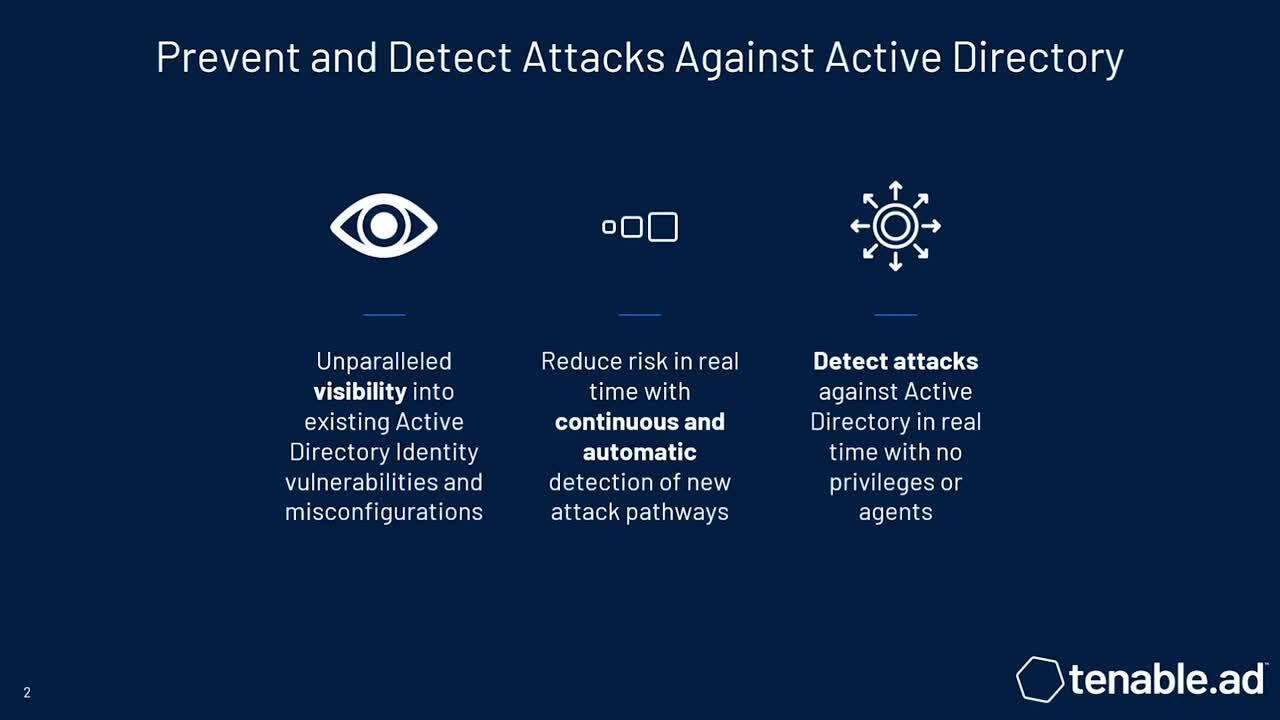

Tenable Identity Exposure
Protect your Active Directory (AD) instance and eliminate potential attack paths with Tenable Identity Exposure. This fast, agentless AD security solution gives complete environment visibility to reduce risk and eliminate vulnerabilities before they’re exploited.

Tenable Vulnerability Management
Understanding what vulnerabilities exist and which ones to prioritize helps you minimize risk. Tenable Vulnerability Management offers a risk-based view of an attack surface to identify, investigate, and prioritize vulnerabilities.
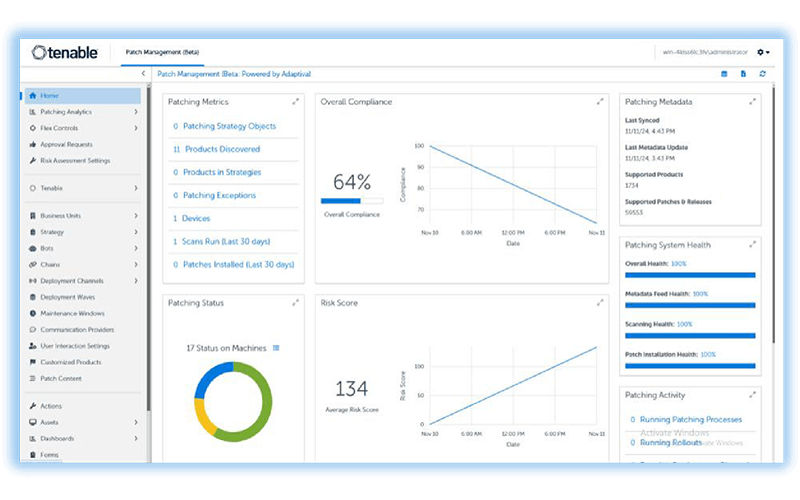
Tenable Patch Management
Are you ready to eliminate vulnerability exposure with enterprise-ready patch management functionality? Stay ahead of threat actors who successfully exploit known vulnerabilities and transition from reactive to proactive remediation with Tenable Patch Management.
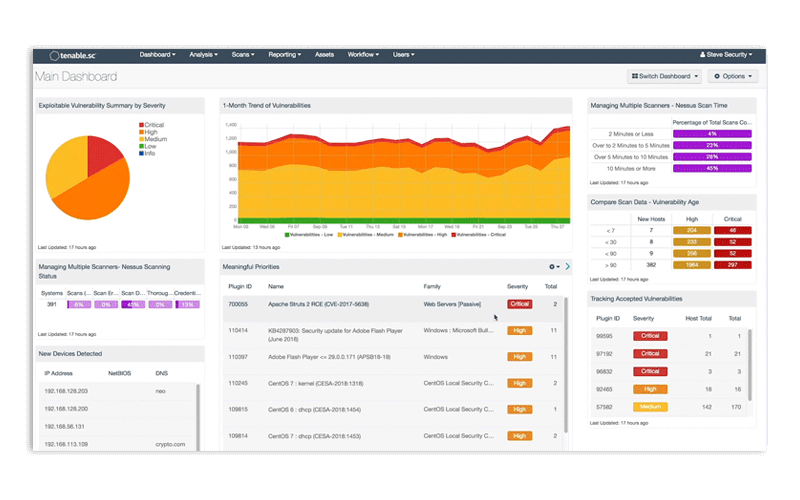

Tenable Security Center
Understanding what vulnerabilities exist and which ones to prioritize helps you minimize risk. Tenable Vulnerability Management offers a risk-based view of an attack surface to identify, investigate, and prioritize vulnerabilities.


Tenable Security Center Plus
To effectively manage and reduce cyber risk, organizations need a vulnerability management solution that provides complete visibility into the attack surface.
Tenable Security Center Plus is a leading vulnerability management platform that reduces organizational risk through advanced analytics, customizable dashboards, reports, and workflows.
Tenable Nessus
The Tenable Nessus® vulnerability assessment solution is designed to protect the modern attack surface and safeguard your organization from cyberthreats.

Tenable Nessus Professional
Cybercriminals work fast, making it tough for organizations with limited resources to keep their assets safe. Reduce risk using Nessus to proactively find and fix vulnerabilities across your constantly changing attack surface.


Tenable Nessus Expert
Tenable Nessus Expert streamlines vulnerability assessments by rapidly detecting and resolving vulnerabilities, including software flaws, missing patches, malware and misconfigurations across a variety of operating systems, devices, and applications.



