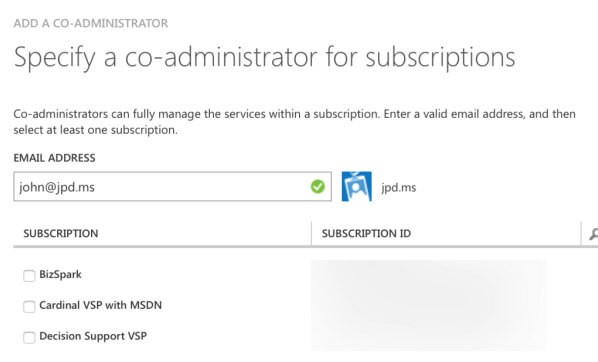
... and organizational accounts resolve as org accounts.
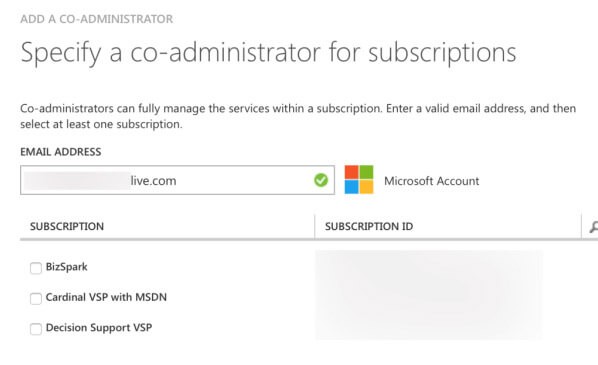
Once you’ve typed in the proper account that needs access, check the boxes next to the subscription(s) you want that account to be able to co-adminster. If the name resolves, you’re finished.
Managing another org’s subscription
Take this scenario: you're a managed service provider offering Azure resources and subscriptions as part of your management package. This implies you need to sign in to other Azure subscriptions and manage them as a co-administrator. But your organizational account is already using Azure AD, so you (and any of your employees) still need to use organizational accounts to administer customer subscriptions (instead of MSAs). Fortunately, it’s possible, but with a few more hoops.
Here are some dummy account names to make this more concrete:
- Your business is Super Azure Consultancy, or SAC, and your domain is @sac.local (this deliberately won’t resolve and won’t be a domain you’ll find in any Azure AD tenant. The domains need to be internet-resolvable).
- You offer managed Azure subscriptions to your clients. Client A is Larsen’s Biscuits, @larsen.local.
- Larsen’s has an Azure subscription tied to its Azure AD tenant (per the instructions in the section above).
- You need to have your employee, mark@sac.local, administer Larsen’s Azure subscription using his @sac.local account.
Getting another Org’s users into your tenant
Add a user from tenant A to tenant B.
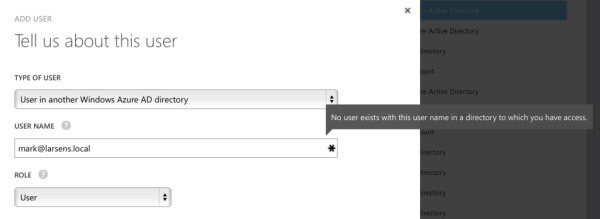
First, we need to add mark@sac.local to the larsen.local Azure AD tenant. This sounds simple on the surface, but it's a bit trickier. In short, you need to sign in to the Azure management portal with an account that has access to both the source directory (sac.local) and the target directory (larsen.local). This is likely easiest using an MSA.
Either create or use an MSA and add that MSA as a global administrator to each Azure AD tenant, not just the Azure subscription (see instructions on how to do that).
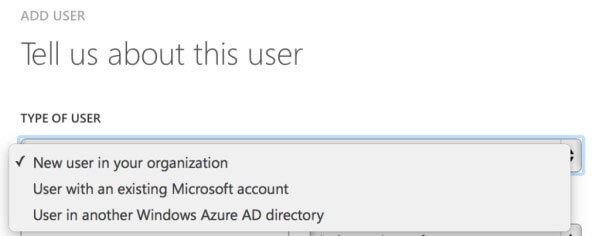
Next, we need to add Mark (mark@sac.local) to the Larsen tenant. Head into Azure AD in the Management Portal, click Users and then Add: