Security begins at startup.
From the moment you turn on your computer, malware can enter and infect your system from a plethora of avenues — even before you reach the welcome screen. Malware, such as a rootkit, is designed to sneak in by replacing your boot loader and then load your normal Operating System (OS) while the malware remains in your system, invisible.
You can help maintain the integrity of your system by detecting malware before startup with Intel Boot Agent and Windows 10 Secure Boot, which uses the Unified Extensible Firmware Interface (UEFI). These built-in defenses at the hardware and software levels ensure only a white list of trusted software can run during startup and boot your PC safely.
In most cases, an OS will trust an application by default. Windows 10 Device Guard requires applications to earn trust before they’re permitted to run. Intel virtualization security and hardware-based isolation enable Device Guard to lock down a device and prevent untrusted or unauthorized executables from running, protecting the system core and drivers from malware and zero-day exploits.
When it comes to data security, IT professionals agree the surest path to true information protection is through encryption. When you use encryption, lost or stolen devices — including hard drives — don’t become a liability.
Among many new security measures, the Windows 10 Anniversary Update also includes a newer version of its own encryption tool called Bitlocker. Integrated into the OS, Bitlocker offers easy and automatic data encryption. Using Intel’s Trusted Platform Module (TPM) 2.0 hardware, Bitlocker can speed the encryption process with low Central Processing Unit (CPU) usage. It also uses the TPM-based hardware for preboot authentication and Single Sign-on (SSO), protecting the device from bypass attacks.
Intel’s TPM acts as a last line of defense. In the event of a stolen or compromised hard drive, stored secrets such as encryption keys and passwords are in a secured chip, impenetrable to hackers.
The strongest password is no password.
Perhaps one of the most frustrating user experience elements of security is having to create — and remember — numerous passwords. But there’s a greater problem than your memory when it comes to passwords: They’re not impenetrable. Verizon’s 2017 Data Breach Investigations Report found that 81% of hacking-related breaches that occurred among the 65 companies interviewed were due to stolen and/or weak passwords.2
Windows 10 security replaces passwords with Windows Hello, a biometric security advantage using facial recognition, iris scans or fingerprint readers. To accomplish this, Windows software leverages special hardware such as Intel RealSense infrared cameras.
Once authenticated, Windows Hello links with Microsoft Passport to grant permissions for the device to other connected applications and web services. Only one method of authentication is required. However, IT teams can implement policies modulating levels of security authentication by user location. For example, one-factor security would be fine for an on-premise employee, whereas remote employees outside the office may require two-step authentication, and login attempts outside the country may require three steps.
Windows Hello is identity protection already integrated into the OS, so it’s easy to deploy and use with no passwords to remember. And, most importantly, it cannot be stolen by hackers.
Win with hardware and software cyber defense.
“The beauty of the Intel and Microsoft relationship is that we have our engineers and architects sit down and talk about the future and make sure the hardware and software work together,” says Hubbard.
The new Windows 10 security included in the Anniversary Update, together with Intel hardware protections, provides formidable cyber defense for an all-in-one solution. The Intel and Microsoft partnership creates better integration for both hardware and software.
Old hardware, however, does not support new software security features. To take advantage of next-generation cybersecurity against advanced threats, you’ll need to upgrade your hardware — an investment, Hubbard argues, that’s well worth the price compared to the alternative of a cyberattack.
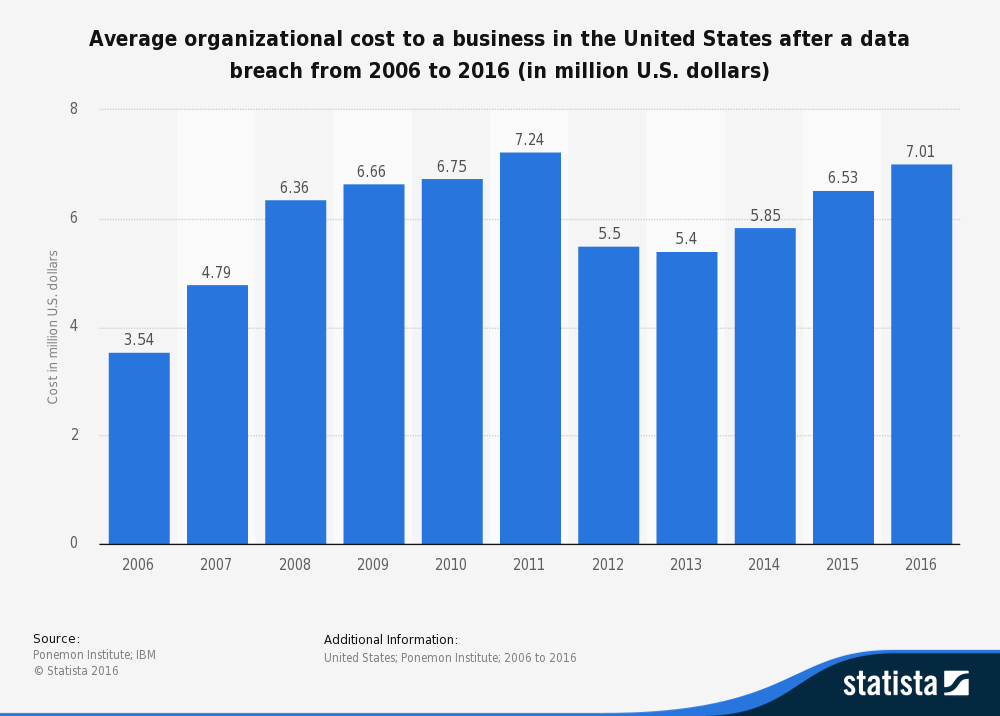
1 Ponemon Institute. (June 2017). 2017 Cost of Data Breach Study. 2 Verizon. (2017). 2017 Data Breach Investigations Report, 10th Edition.