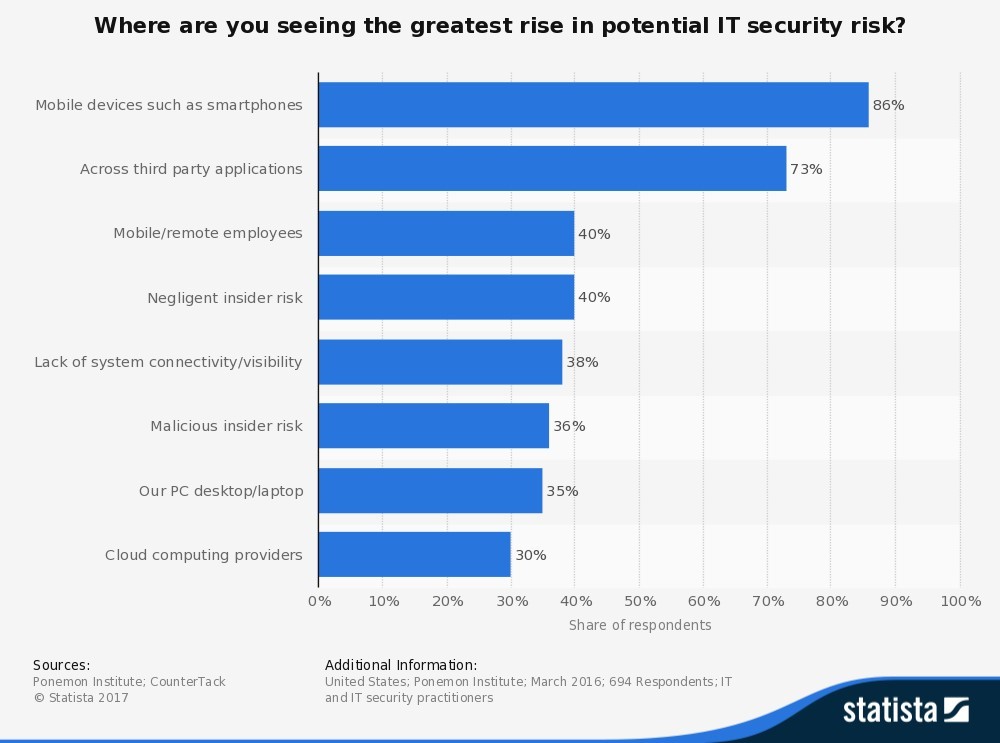
Figure 1 depicts the results from a survey that the Ponemon Institute conducted in 2016, asking 694 IT professionals in the United States, “Where are you seeing the greatest rise in potential IT security risk?” 86% declared that mobile devices, such as smartphones, were the biggest threat to endpoint security. Subsequently, 73% said across third party applications and 40% said mobile/remote employees. While we have grown accustomed to the many noticeable benefits of the BYOD movement — such as greater job satisfaction and flexibility — it’s still necessary to take steps to ensure that client information, employee credentials and organizational data are secure.
Enterprise Mobility + Security has you covered.
Microsoft Enterprise Mobility + Security (EMS) provides flexible, comprehensive solutions that help businesses empower employees to access all of their data and applications from every device and every location. With EMS, you get complete access to services that will help you:
Control identity and access in the cloud.
- Get identity-driven security.
- Protect your corporate data.
- Enable secured collaboration.
- Manage mobile devices and applications.
With EMS, you not only protect data that is vital to the success of your organization, but also identify where security breaches might occur before they damage your finances or reputation.
Device security is a must.
Let’s take a moment to focus on mobile device and applications management. Microsoft Mobile Application Management (MAM) and Mobile Device Management (MDM) solutions are designed to help businesses easily deliver administrative capabilities either on premises, in the cloud or through a hybrid platform — all from one console.
When you choose EMS, you are choosing a more secure and seamless transition to a primarily mobile-driven environment. With the EMS E3 bundle, you also gain access to best-in-class Microsoft solutions to better protect data.
Windows Intune: Your employees want their personal devices to seamlessly integrate with their work requests. The faster they are able to log in to the company’s system, the sooner they can start assisting clients. That means you need an operating system that will ensure user devices remain compliant while enabling IT to securely register and manage applications across multiple sectors. Windows Intune is your hassle-free guide to greater workforce security and enablement.
Azure Active Directory Premium (AADP): Remembering a handful of passwords can be challenging and frustrating. With AADP, you get a single identity and password for all approved internal and third-party applications. Plus, self-service password resets reduce the cost of IT support. What if a suspicious individual figures out the login information of one of your teammates? AADP advanced reporting alerts will make sure you’re notified that an unconventional IP address or device is trying to infiltrate the system.
Azure Information Protection Premium (AIPP): Prioritizing endpoint security is a must — this includes phones, tablets, laptops and printers. But what happens if a hacker somehow manages to slip through your defenses? It’s important to be extra cautious and make sure that those who sneak in can’t do anything with your data once they’ve accessed it. That’s why AIPP allows users to specify who can open, modify, print or forward content.
Advanced Threat Analytics (ATA): While it’s important to have a backup plan like AIPP, it’s equally important to have a preventive plan in place to identify advanced persistent threats before they occur. ATA uses behavioral analytics to provide an actionable report to help your business quickly take action.