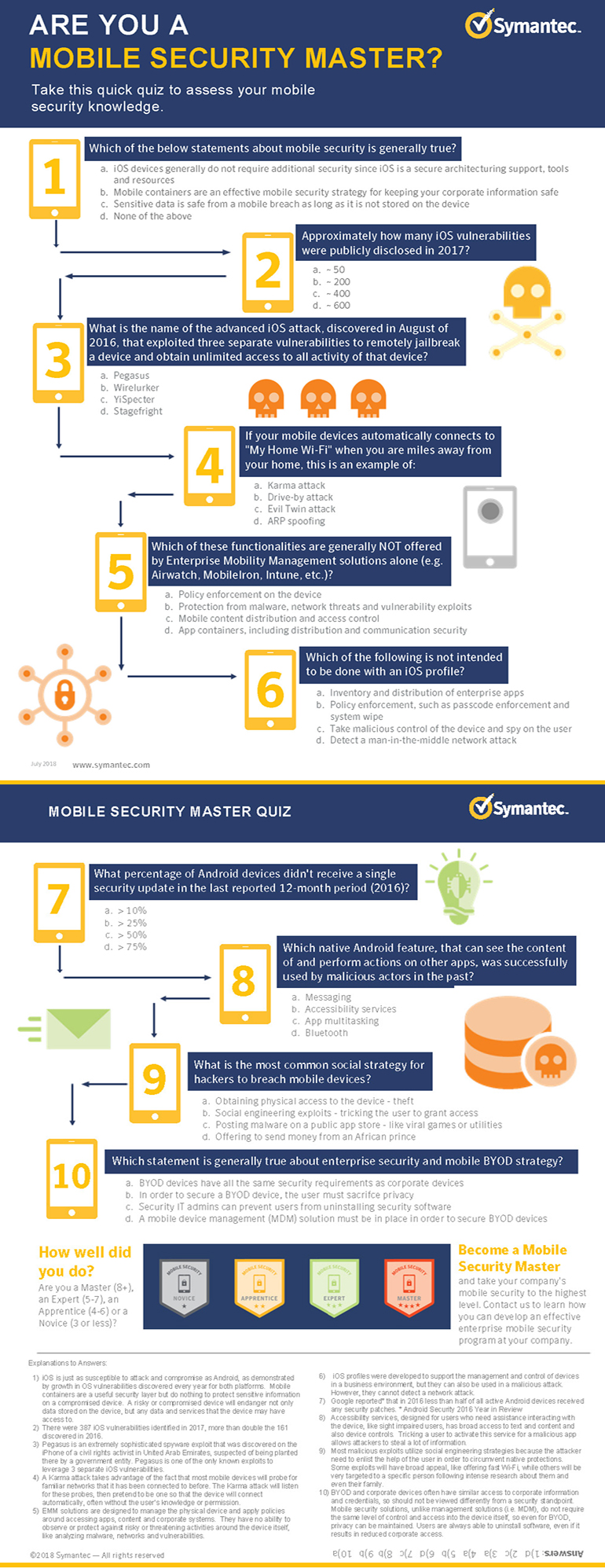
Infographic Are You a Mobile Security Master?
As mobile devices take on more instrumental roles in the workplace, threats to these vulnerable endpoints can pose serious risks. Yet many critical elements of a mobile security program are easy to overlook. Take this assessment to find out how your mobile security knowledge stands up to the facts.
Accessibility note: The infographic is translated below the graphic.
By Insight Editor / 23 Aug 2018