Resilient Zero Trust
Manage and secure data, devices and applications with the Absolute® security platform, available from Insight. You’ll unlock an unbreakable connection to every endpoint — on or off your network.
Secure your distributed workforce.
Absolute security gives you the peace of mind that comes with complete visibility and control over data, devices and applications.
Asset intelligence
You'll gain the power to monitor and manage endpoints, on and off the enterprise network.
Self-healing
Absolute is embedded in all your devices for always-on, automated remediation.
Proven compliance
Constant protection helps you remediate security risks before they affect your organization.
Unrivaled device protection
Dark endpoints leave your most vital business data vulnerable. See how the Absolute platform, embedded in more than 500,000 million endpoints, empowers IT to identify and resolve risks.

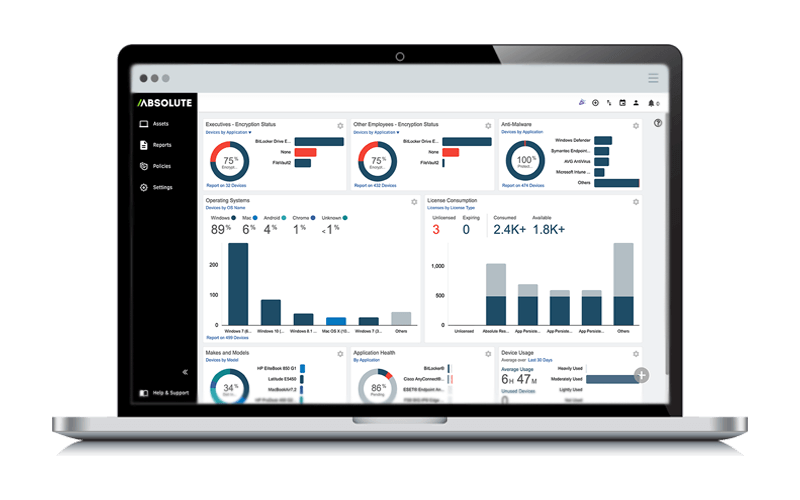
Expand your visibility.
Now you can gain a full view of your distributed workforce — and unparalleled control over every endpoint. Absolute lets you quickly recognize, understand and act upon risky behavior, so you can safeguard your IT assets.
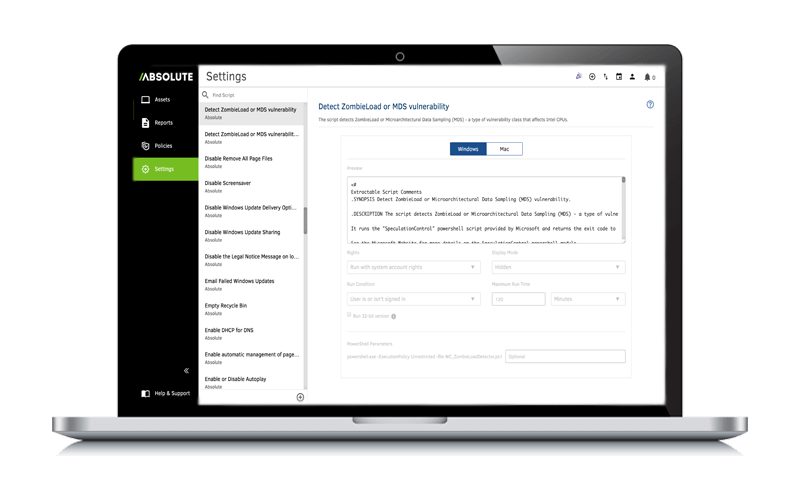
Enable self-healing.
With firmware-embedded technologies, you can unlock zero-touch healing. The Absolute platform keeps you constantly connected to every device and eliminates downtime for your critical applications.
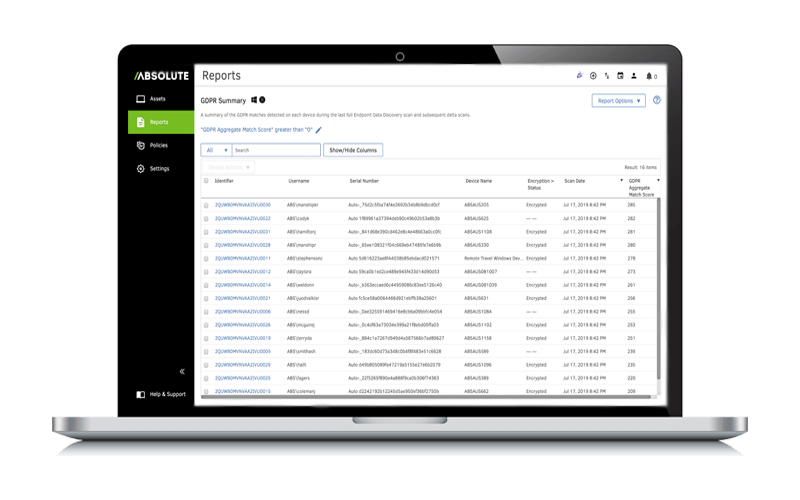
Compliant and audit-ready
Effective data governance helps you stay ahead of changing regulatory and privacy demands. The Absolute platform expands your visibility over sensitive data and lets you manage security risks through one centralized console.